MAC address filtering allows you to define a list of devices and only allow those devices on your Wi-Fi network. That’s the theory, anyway. In practice, this protection is tedious to set up and easy to breach.
MAC address filtering allows you to define a list of devices and only allow those devices on your Wi-Fi network. That’s the theory, anyway. In practice, this protection is tedious to set up and easy to breach.
Mac Filtering Xbox
This is one of the Wi-Fi router features that will give you a false sense of security. Just using WPA2 encryption is enough. Some people like using MAC address filtering, but it’s not a security feature.
How MAC Address Filtering Works
RELATED:Don’t Have a False Sense of Security: 5 Insecure Ways to Secure Your Wi-Fi
Each device you own comes with a unique media access control address (MAC address) that identifies it on a network. Normally, a router allows any device to connect — as long as it knows the appropriate passphrase. With MAC address filtering a router will first compare a device’s MAC address against an approved list of MAC addresses and only allow a device onto the Wi-Fi network if its MAC address has been specifically approved.
Mac Filtering Turn Off
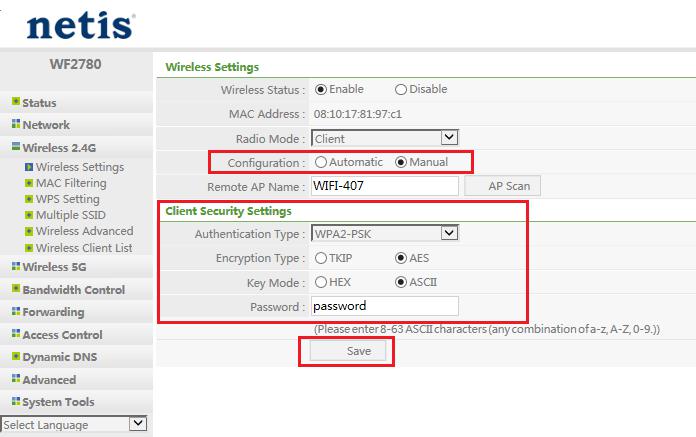
Your router probably allows you to configure a list of allowed MAC addresses in its web interface, allowing you to choose which devices can connect to your network.
MAC Address Filtering Provides No Security
So far, this sounds pretty good. But MAC addresses can be easily spoofed in many operating systems, so any device could pretend to have one of those allowed, unique MAC addresses.
MAC addresses are easy to get, too. They’re sent over the air with each packet going to and from the device, as the MAC address is used to ensure each packet gets to the right device.
RELATED:How an Attacker Could Crack Your Wireless Network Security
The quotation list displays the resulting 6 quotations that contain all comments written by parents of teenage kids. Atlas ti manual for mac os.
All an attacker has to do is monitor the Wi-Fi traffic for a second or two, examine a packet to find the MAC address of an allowed device, change their device’s MAC address to that allowed MAC address, and connect in that device’s place. You may be thinking that this will not be possible because the device is already connected, but a “deauth” or “deassoc” attack that forcibly disconnects a device from a Wi-Fi network will allow an attacker to reconnect in its place.
We’re not exagerating here. An attacker with a toolset like Kali Linux can use Wireshark to eavesdrop on a packet, run a quick command to change their MAC address, use aireplay-ng to send deassociation packets to that client, and then connect in its place. This entire process could easily take less than 30 seconds. And that’s just the manual method that involves doing each step by hand — never mind the automated tools or shell scripts that can make this faster.
WPA2 Encryption Is Enough
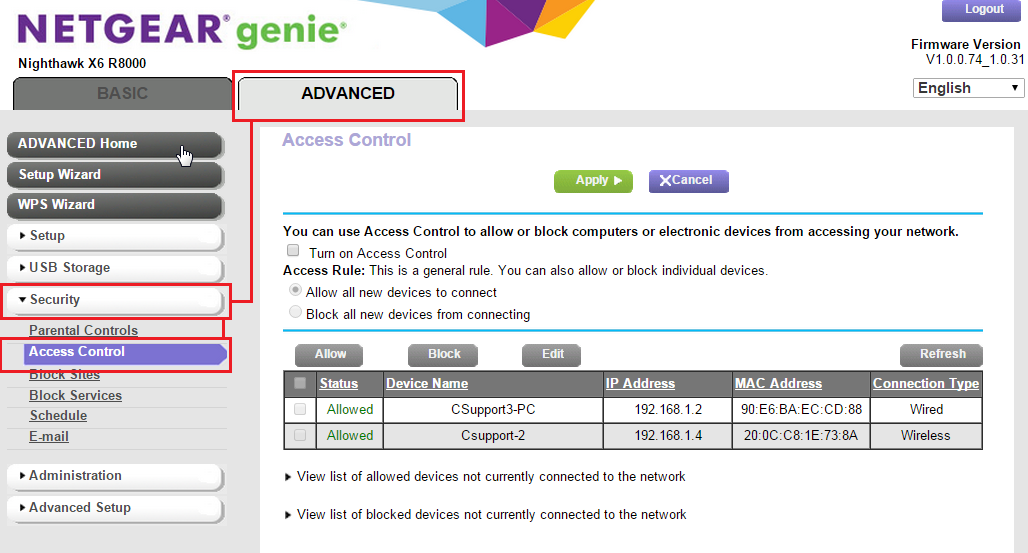
RELATED:Your Wi-Fi’s WPA2 Encryption Can Be Cracked Offline: Here’s How
At this point, you may be thinking that MAC address filtering isn’t foolproof, but offers some additional protection over just using encryption. That’s sort of true, but not really.
Basically, as long as you have a strong passphrase with WPA2 encryption, that encryption will be the hardest thing to crack. If an attacker can crack your WPA2 encryption, it will be trivial for them to trick the MAC address filtering. If an attacker would be stumped by the MAC address filtering, they definitely won’t be able to break your encryption in the first place.
Think of it like adding a bicycle lock to a bank vault door. Any bank robbers that can get through that bank vault door will have no trouble cutting a bike lock. You’ve added no real additional security, but every time a bank employee needs to access the vault, they have to spend time dealing with the bike lock.
It’s Tedious and Time-Consuming
RELATED:10 Useful Options You Can Configure In Your Router’s Web Interface
The time spent managing this is the main reason you shouldn’t bother. When you set up MAC address filtering in the first place, you’ll need to get the MAC address from every device in your household and allow it in your router’s web interface. This will take some time if you have a lot of Wi-Fi-enabled devices, as most people do.
Whenever you get a new device — or a guest comes over and needs to use your Wi-Fi on their devices — you’ll have to go into your router’s web interface and add the new MAC addresses. This is on top of the usual setup process where you have to plug in the Wi-Fi passphrase into each device.
This just adds additional work to your life. That effort should pay off with better security, but the miniscule-to-nonexistent boost in security you get makes this not worth your time.
Use only the electrical cord supplied by HP with the printer. Do not damage, cut or repair the power cord. A damaged power cord can cause fire or electric shock. Replace a damaged power cord with an HP-approved power cord. Do not allow metal or liquids (except those used in HP Cleaning Kits) to touch the internal parts of the printer. Feb 15, 2013 Question: Q: I can't select the manual feed tray for my HP printer. I have a MacBook with Mac OsX Lion and I have an HP Officejet J6480 All-in-One printer. My cardstock keeps jamming and everything I've read says I should use the manual tray, but I. I print a lot of documents from the manual feed tray. I just changed to a new computer. On my old computer, whenever I wanted to print to the manual feed tray, I would choose the appropriate paper source from the page setup menu in MS Word - both first page and other pages (I was using 2007 version, I am now using 2013 version). Mac cant print to manual feed hp t2300. The printer does not print. If you are using Mac OS with a USB connection, you may find that you need to change the data encoding (T2300 PS only). Press, then, then Setup Printing preferences PS Select encoding ASCII. Then configure your application to send ASCII data. HP DesignJet T2300 Multifunction Printer Choose a different product Warranty status: Unspecified - Check warranty status Manufacturer warranty has expired - See details Covered under Manufacturer warranty Covered under Extended warranty, months remaining month remaining days remaining day remaining - See details.
This Is a Network Administration Feature
MAC address filtering, properly used, is more of a network administration feature than a security feature. It won’t protect you against outsiders trying to actively crack your encryption and get onto your network. However, it will allow you to choose which devices are allowed online.
Manual Mac Filtering Software
For example, if you have kids, you could use MAC address filtering to disallow their laptop or smartphpone from accessing the Wi-FI network if you need to ground them and take away Internet access. The kids could get around these parental controls with some simple tools, but they don’t know that.
That’s why many routers also have other features that depend on a device’s MAC address. For example, they might allow you to enable web filtering on specific MAC addresses. Or, you can prevent devices with specific MAC addresses from accessing the web during school hours. These aren’t really security features, as they’re not designed to stop an attacker who knows what they’re doing.
So it is with this 'Board, and raising a topic as you did gives a number of us a chance to brainstorm and visit, albeit from afar. So, I'd lean against the outside shop wall of a summer morning or afternoon and listen to the oldtimers as they'd 'build' all kinds of stuff. It's a rainy morning, kind of bleak, so kicking back for a few minutes to swill more coffee and think of a chipper shredder is the thing to do.As a high-school aged young buck working the oldtime machine shops in summers, I learned quick enough that coffee time (int he mornings) or beer time (afternoon breaks- we used to be handed a quart of beer apiece), were the times the oldtimers gathered and 'built jobs'. Of course, out in AZ, I doubt you would be having reason to hang around a woodstove of a winter's day.As I type this, before getting into the day;s work here, I've got my third cup of 'bunker C' or 'Tugboat coffee'- straight black. How much of it ever becomes real hard iron is some infintesimal fraction of what got 'built' around the stove. Mighty mac chipper parts.
If you really want to use MAC address filtering to define a list of devices and their MAC addresses and administer the list of devices that are allowed on your network, feel free. Some people actually enjoy this sort of management on some level. But MAC address filtering provides no real boost to your Wi-Fi security, so you shouldn’t feel compelled to use it. Most people shouldn’t bother with MAC address filtering, and — if they do — should know it’s not really a security feature.
Image Credit: nseika on Flickr
READ NEXT- › How to Enable Google Chrome’s New Extensions Menu
- › How to Stop Spammers From Attacking Your Google Calendar
- › How to Power Off Your Samsung Galaxy Note 10 or 10 Plus
- › How to Switch from a Windows PC to a Mac
- › Want to Survive Ransomware? Here’s How to Protect Your PC